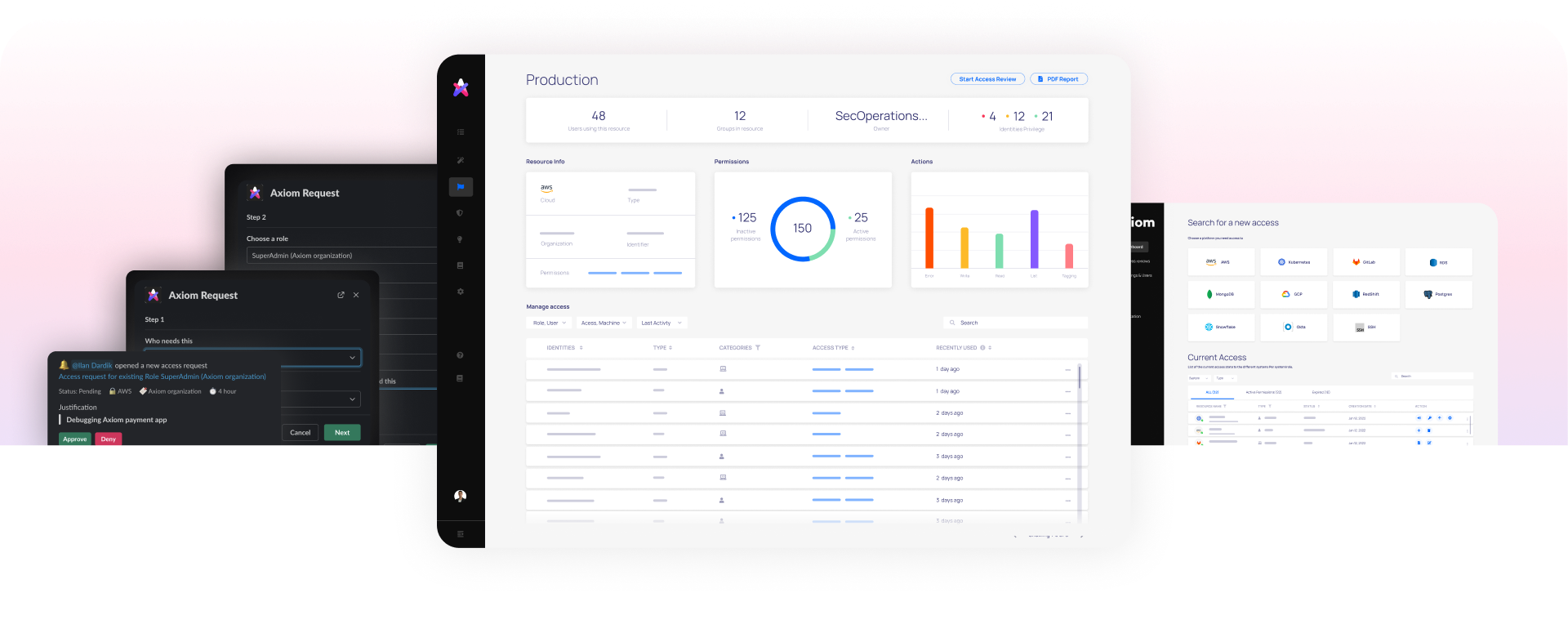



Enable zero-touch approvals while putting guardrails on sensitive environments

Instantly give users the just-in-time, right-sized permissions they need

Understand which permissions are increasing the attack surface and what should be done to mitigate them

See and manage who has access where, across all systems, and what they can do with their permissions

Works with the tools you already have for easy, effective collaboration

Axiom continuously learns normal behavioral patterns to better alert on anomalies and prevent malicious actions

Seamless on-boarding and integrations, with no deployment required. All of our services are hosted in AWS.

You can self-host the data plane behind your own VPN and in your own VPC.
© Copyright 2022, All Rights Reserved by Axiom Security